- Vulnerability Scanner In Kali Linux
- Vulnerability Scanner Open Source
- Vulnerability Scanner
- Vulnerability Scanner Tools

Formerly Retina Network Security Scanner - Reduce risk with cross-platform vulnerability assessment and remediation, including built-in configuration compliance, patch management and compliance reporting.
Get a full website security check for known vulnerabilities and HTTP security headers
- Vulnerability scanners have a database of vulnerabilities based on which it performs the check on the remote host. The vulnerability database contains all the information required (service, port, packet type, a potential path to exploit, etc.) to check the security issue. They can scan the network and websites against thousands of.
- Vulnerability scanning is a vital part of your security team’s overall IT risk management approach for several reasons Vulnerability scanning lets you take a proactive approach to close any gaps and maintain strong security for your systems, data, employees, and customers.
Snyk free website vulnerability scanner performs a passive web security scan in order to detect issues like: outdated server software and insecure HTTP headers.
Today, vulnerability management is no longer a nice-to-have but rather a critical requirement for anyone running web applications or interactive and static websites. These kinds of public-facing assets are common attack vectors for malicious actors seeking unauthorized access to systems and data. Vulnerability scanning helps to minimize risk and control vulnerabilities from the very beginning of website development.
Vulnerability scanner monitors for misconfigurations or vulnerable third-party open-source dependencies that pose cybersecurity threats. Online vulnerability scanners either rely on a database of known vulnerabilities or probe for common flaw types to discover unknown vulnerabilities. Website scanner scanner logs detect vulnerabilities and assigns a risk score.
Security scores are based on two core metrics:1. Vulnerable versions of JavaScript libraries which were detected on the page and pose a potential security threat.2. Security headers, in which we check which HTTP security headers have been set for the website, and those which are missing but recommended to turn on.The highest grade you can get is an A+ and the lowest is an E.
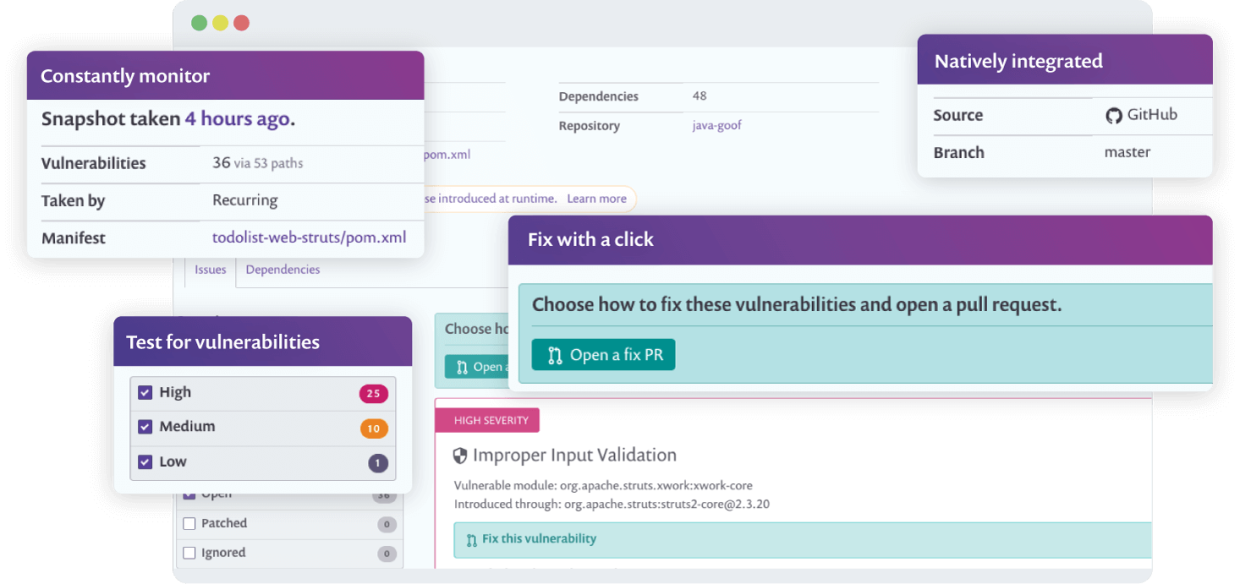
You’ve scanned your website for vulnerabilities, it’s time to take the next step!
Sign up for Snyk to find, fix and monitor your vulnerabilities.


Vulnerability Scanner In Kali Linux
Find vulnerabilities early and
across the SDLC
- Broad ecosystem support Languages
- Wide set of IDE integrations
- Native Git scanning
- CI/CD gating
- Production environment
Get started with Snyk for free. No credit card required.
Vulnerability Scanner Open Source
In today’s hyper-connected world, reports of cyber-attacks and data breaches are commonplace. On any given week of the year, you can count on seeing news reports of the latest cyber incident. With the average total cost of a data breach coming in at an astounding $3.92 million (according to the latest analysis by IBM), you can understand why cyber security is an increasing concern for businesses all over the world.
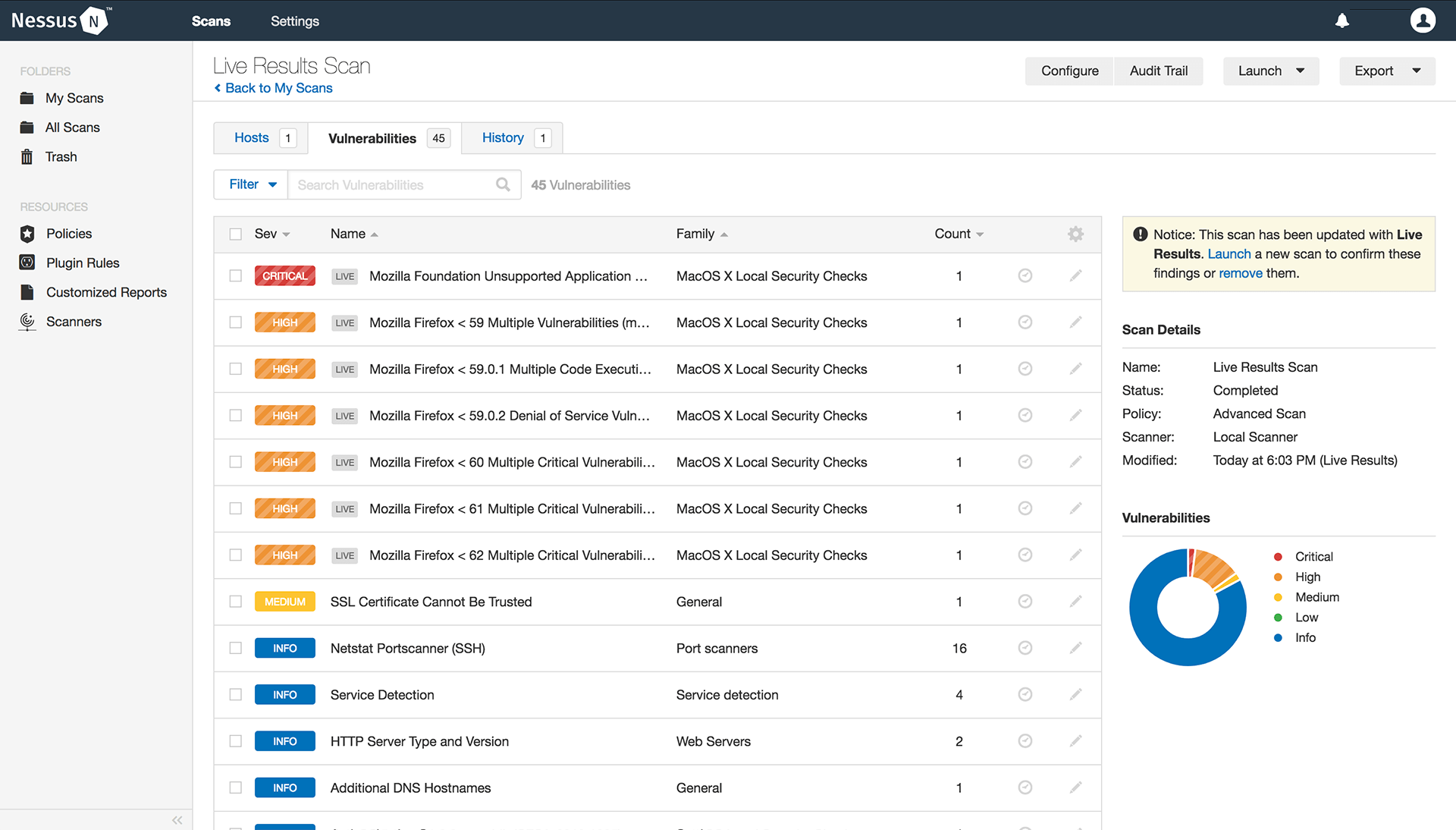
Vulnerability Scanner
Vulnerability scanning is a fundamental component of all good cyber security strategies, but it can be complicated, and challenging to get right. Whether your organisation is just starting out on its journey to becoming more secure, or you’re looking to improve on existing security controls and learn more about vulnerability scanning best practices, this guide has something for you.
Vulnerability Scanner Tools
In this guide, you'll learn about: what is vulnerability scanning, the different types of vulnerability scanners available, vulnerability scanning frequency best practices, how to choose a vulnerability scanner, and how to get up and running with your chosen product. So let's get started.